
Identify
Peritus Digital understands that in today's connected world, its only a matter of time when a cyber security incident will occur. Thankfully, there are frameworks in place that have been designed to reduce and limit an organisations risk and remain productive.
Peritus Digital follows the ASD Essential 8 and NIST cyber security framework to ensure we are delivering services that matter. With our solutions in place, you can focus on what you do best—running your business—while we handle the rest.
By adopting these methodologies and tools, you are also reducing your cyber security insurance bill

Understanding what you want to protect or what you consider valuable in the digital world can be daunting. At Peritus Digital, we are here to help.
In the NIST framework, Data classification is a crucial aspect of the "Identify" component. Peritus Digital can assist clients on their security improvement journey to categorise data assets based on their value, sensitivity and importance to their business.
This process will help businesses to implement appropriate security controls and safeguard risks based on the level of risk associated with each type of data.

Governance, Risk, and Compliance (GRC) with Peritus Digital involves integrating governance, risk management, and compliance activities to ensure that organisations effectively manage cybersecurity risks, comply with relevant standards and regulations, and align their security practices with NIST's best practices and guidelines.
This approach helps businesses strengthen their cybersecurity posture, protect their information assets, and achieve their business objectives in a secure and compliant manner.

How secure is your organisation? If your business has invested heavily with Cyber Security, NOW is the time to put those defences and processes to the test.
Peritus Digital understands the nuances that penetration testing (Ethical hacking) entails.
Penetration testing plays a critical role in the security lifecycle by identifying and addressing security vulnerabilities and weaknesses in IT systems and networks. Peritus Digital will assist business in understanding the areas that are suseptible to compromise (vulnerable) and advise on remediation.
This will strengthen your cybersecurity defences and mitigate the risk of real-world cyberattacks

Having Peritus Digital perform your vulnerbility testing will help your organization proactively identify and address security weaknesses.
Peritus Digital will work with your organisation to mitigate the risk of exploitation by malicious actors and enhance overall cybersecurity posture.
This process typically involves using automated tools to scan for known vulnerabilities, categorizing them based on severity and impact, and providing recommendations for remediation.
4 Steps of the Vulnerability Management Process
- 1. Perform Vulnerability Scan
- 2. Assess Vulnerability Risk
- 3. Prioritize & Address Vulnerabilities
- 4. Continuous Vulnerability Management

Breach and Attack Simulation (BAS) is a proactive cybersecurity technique used to simulate real-world cyberattacks on an organization's IT infrastructure, networks, and applications.
Peritus Digital will work with your organisations team to emulate various attack scenarios, including malware infections, phishing campaigns, and insider threats, to assess the effectiveness of existing security controls and identify potential vulnerabilities.
By mimicking the tactics, techniques, and procedures (TTPs) used by threat actors, Peritus Digital will be able to validate your organisations security posture, identify gaps in defences, and prioritise remediation efforts based on actionable insights.
Protect
Zero Trust - No one is trusted by default from inside or outside the network, and verification is required from everyone trying to gain access to resources on the network.
The Essential Eight is a highly regarded migration strategy developed by the Australian Signals Directorate (ASD) to help protect organisations against a wide variety of cyber threats.
Peritus Digital have the skills and knowledge to guide your business with our technical expertise to proactively implement and ultimately prevent and/or limit the extent of an attack.
- 1. Application Control
- 2. Patch Applications
- 3. Configure Microsoft Office Macro settings
- 4. User Application hardening
- 5. Restrict Administrative Privileges
- 6. Patch operating systems
- 7. Multi-Factor Authentication (MFA)
- 8. Daily Backups

Peritus Digital offers the best in breed, enterprise firewalls to protect the perimeter / internet edge.
The goal is to create a barrier that prevents unauthorized access while allowing legitimate traffic to pass through. Perimeter security measures include:
The Essential Eight is a highly regarded migration strategy developed by the Australian Signals Directorate (ASD) to help protect organisations against a wide variety of cyber threats.
- 1. Firewalls: Virtual and or Physical Firewalls are network security devices that monitor and control incoming and outgoing traffic based on predetermined security rules.
- 2. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS are security tools that monitor network traffic for suspicious activity or known attack patterns.
- 3. Virtual Private Networks (VPNs): VPNs create encrypted connections over the internet, allowing remote users to securely access the organization's network resources. They help protect data as it travels between remote devices and the corporate network.
- 4. Demilitarized Zone (DMZ): A DMZ is a network segment that sits between an organization's internal network and an external network, such as the internet. It hosts services that need to be accessible from the internet, such as web servers, while providing an additional layer of security by isolating them from the internal network.
- 5. Network Segmentation: Network segmentation involves dividing a network into smaller subnetworks or segments to control the flow of traffic and contain potential breaches. It limits the impact of security incidents by isolating sensitive assets from less secure areas.

Threat intelligence can compliment and enhance existing cyber protections. Combine your perimeter defences with Peritus Cyber Threat Intelligence which gathers intelligence from a wide range of sources about current or potential attacks against an organisation.
This information is then assessed with an action taken which is to predominately block or monitor depending on the information available.
Threat Intelligence is mostly comprised of;
- 1. IP Addresses
- 2. Domain Names
- 3. SHA-256 (Files)
- 4. URL’s (HTTP/HTTPS)
Sources can be Security Intelligence Providers (e.g. Security Vendors (E.g. Talos), Advisories/Alerts (CISA, ACSC)).

Without digital connectivity, we would still be sending mail through Australia Post. In this day and age email is going strong being a primary communication channel for businesses and individuals but as always, it is facing an ever evolving threat landscape.
Securing your organisations email is crucial to maintain trust with your customers and suppliers, protect confidential data, intellectual property, and personal information from unauthorised disclosure or exploitation.
At Peritus Digital, we excel at all things email.
Helping customers ensure their email authentication (SPF/DKIM/DMARC) is compliant to industry standards ensures your business is sending email from who you legitimately approve of, no more wondering as to why your email was quarantined.
We have also partnered with key AI/ML vendors to ensure those AI generated emails no longer make it through to a users inbox.
Peritus Digital have the skills and knowledge to guide your business with our technical expertise to proactively implement and ultimately prevent and/or limit the extent of an attack.
Gone are the days where worrying about what Joe from accounting was looking at. At Peritus Digital, Web and DNS Security is so much more.
When the Internet was built, computers weren't mobile. They sat in offices next to data centers. The Internet has changed but the assumptions made 30 years ago are making your experience slower and less secure.
Peritus DNS Secure Servers replaces the connection between your device and the Internet with a modern, optimized, protocol.
Your Internet service provider can see every site and app you use—even if they're encrypted. Some providers even sell this data, or use it to target you with ads.
Peritus Digital DNS Secure prevents anyone from snooping on you by encrypting more of the traffic leaving your device.
We believe privacy is a right. We won't sell your data, eve

Endpoint security is your last line of defence in your multi layered approach to (defending) de-risking your business environment.
Endpoint protection solutions work by examining files, processes, and system activity for suspicious or malicious indicators (Looking for the bad guys).
Traditional antivirus solutions detect less than half of all attacks. They function by comparing malicious signatures (or code) to a database that is updated by a variety of sources whenever a new malware signature is identified. The problem is the malware that hasn't been detected yet.
Prevention is not enough. No defences are perfect, and some attacks will always make it through and successfully penetrate the network. To prevent silent failures, an "Endpoint Detection and response" (EDR) solution needs to provide continuous and comprehensive visibility into what is happening on endpoints in real time.
Peritus Digital will work with your organisation to ensure you have a holistic endpoint security solution that will successfully stop breaches including true next-generation antivirus and EDR, managed threat hunting, and threat intelligence automation

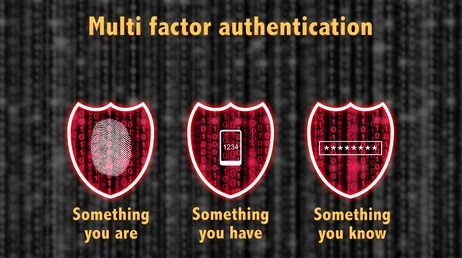
Can you truly trust that it was Joe logging into the system? Zero Trust? Consider multi-factor authentication and identity management.
As one of the essential 8, multi-factor is one of the most important investments your organisation can make to mitigate unauthorised access within your environment.
It is almost everywhere these days and the ones without are leaving the proverbial door wide open.
Peritus Digital has parted with multiple MFA and identity management solutions to work with your organisation to meet business needs and compliance whilst also ensuring employees are not overload with identity fatigue.
The walls have fallen, you have been breached. Can you recover?
Data backups are key to ensuring your business is survivable during an event.
Events can be simple, requiring data recovery for a mistake, hardware failure, theft, natural disaster, virus or they can be catastrophic, every machine has ransomware.
Recovering data can be expensive and sometimes impossible.
Peritus Digital have the skills and expertise to assess your needs and collaboratively work with your business to develop a strategy and backup solution.
Remember, A solution is only as good as what has been tested and validated on a consistant on-going basis.

Monitor and SOC
Security monitoring and response involve continuously monitoring IT environments to detect and analyze potential security threats, unauthorized access attempts, or suspicious activities. Once identified, appropriate response actions are taken to contain and mitigate security incidents, ensuring the integrity and availability of organizational information assets.
Security defences are not enough to set and forget, they will do a good job but to be fully compliant you need a system watching the environment.
This is where Peritus Digitals Extended Detection and Response (XDR) and Security Information and Event Management (SIEM) solution comes into play.
It is a centralized platform providing a comprehensive security solution that detects, analyzes, and responds to threats across multiple digital infrastructure layers.
Peritus Digitals platform will collect, aggregate and analyse telemetry from endpoints, network devices, cloud workloads, third-party APIs, and other sources for unified security monitoring and protection.

Respond
At Peritus Digital, we understand that cyber-security incidents are not a matter of if, but when they will occur. That's why we're here to help you proactively prepare for and effectively respond to any cyber-security incident with our tailored incident response policy services, aligned with the best practices outlined by the National Institute of Standards and Technology (NIST).
With our expertise in cybersecurity and adherence to NIST guidelines, we'll work closely with your organization to develop a robust incident response policy that is tailored to your unique business needs and regulatory requirements.
Our incident response policy will outline clear roles and responsibilities, establish communication protocols, define incident classification and response procedures, and provide step-by-step guidance for effectively handling various types of cybersecurity incidents. Whether it's a data breach, malware infection, or other security incident, our policy will ensure that your organization is prepared to respond swiftly and effectively to minimize damage and disruption.
Peritus Digital places a strong emphasis on training and awareness. We ensure your incident response team is well-prepared by providing training sessions, drills, and simulations. This ensures that your team can confidently execute the incident response plan when needed.
At Peritus Digital, we take a proactive approach to developing incident response procedures tailored to your organization's specific needs. These detailed steps guide incident response teams through all four phases of the incident response lifecycle: preparation, detection and analysis, containment, eradication and recovery, and post-incident activity.
Beginning with a comprehensive assessment of your cybersecurity posture, we identify vulnerabilities and risks. We then work closely with your stakeholders to understand your unique requirements, regulatory obligations, and industry best practices. Our procedures outline roles, incident classification, communication protocols, and step-by-step guidance for responding to cybersecurity incidents.
Containment, Eradication, and Recovery are integral phases within the Incident Response process.
In the Containment phase, the focus is on preventing the spread of the incident by isolating affected systems or networks and disconnecting them from the rest of the infrastructure to mitigate further damage or unauthorized access.
Following containment, the Eradication phase aims to identify and eliminate the root cause of the incident through thorough analysis and forensic investigation, ensuring the removal of malware, patching vulnerabilities, and reconfiguring systems to prevent recurrence.
Finally, in the Recovery phase, affected systems, networks, and data are restored to a known good state through data restoration from backups, system rebuilding, and reconfiguration, allowing for the gradual resumption of normal business operations while monitoring for any lingering threats or effects.
These structured phases provide organizations with a systematic approach to managing cybersecurity incidents, minimizing their impact, and swiftly restoring normal operations, ultimately bolstering resilience in the face of evolving threats.
Recover
Recovery, in the context of incident response, involves restoring affected systems, networks, and data to a known good state and resuming normal business operations following a cybersecurity incident.
Preparing for a cyber attack? Your organisations recovery is only as good as your Technical Recovery Plan (TRP).
A Technical Recovery Plan (TRP) refers to a documented set of procedures and strategies designed to restore, recover, and resume normal operations of an organisation's information technology (IT) systems and infrastructure following a disruptive event or incident.
Contact Peritus Digital to see how we can assist you with developing your Technical Recovery Plan.

Your business is thriving, your systems are running smoothly, and your data is secure. But what happens when disaster strikes?
Are you prepared to handle the unexpected?
That's where Peritus Digital's disaster recovery strategies come in. We offer a comprehensive suite of solutions designed to ensure the resilience and continuity of your business operations, no matter the circumstances.
But disaster recovery isn't just about technology, it's also about planning and preparedness. That's why Peritus Digital offer business continuity planning services to help you develop comprehensive plans for maintaining essential business functions during and after a disaster.
With incident response procedures and regular testing and training, we ensure that your organisation is ready to handle any situation that comes your way.

Peritus Digitals backup and restore solutions ensure that your critical data and configurations are securely stored and readily available for recovery in the event of a disaster. With automated backup capabilities and robust data retention policies, you can rest assured that your data integrity is maintained.
Looking to leverage the cloud for disaster recovery? Our Disaster Recovery as a Service (DRaaS) solutions provide scalable and cost-effective options for rapidly recovering your IT infrastructure and data in the event of a disaster. With DRaaS, you can minimize downtime and quickly resume business operations with minimal disruption.
Don't wait until it's too late. Protect your business and ensure its continuity with our disaster recovery test restores. With our solutions in place, you can focus on what you do best—running your business—while we handle the rest.



